NetBrain Security Across The Hybrid Network eBook
Security Across the Hybrid Network No-Code Network Security Automation
A report published by the Identity Theft Research Center found that there was a new record for data breaches reported worldwide with over 1800 data breaches - surpassing the previous year total by 68%. Further, as reported on their annual cost of the data breach report, IBM discovered that for those teams without security automation, it took them an average of 239 days to even discover that their cloud 239 networks were breached. Then it took them an additional 85 days to contain the breach. days to identify average cloud breach1 That's 324 total days under a breach, and even longer for a return to normal operations. What does this mean in terms of impact? Well, one way to classify loss is financial cost. 324 1 In 2022, IBM reported in that same report that the global average cost days to contain of a single data breach was $4.35 million, and that picture looks even worse in the U.S., where that figure more than doubles to $9.44 1 million. According to IBM Security Across the Hybrid Network | 1
Challenges Security Teams are Facing Deployment of advanced security technologies can create the illusion of comprehensive protection, but all too Complex networks often, subsequent changes to the infrastructure can increase risk. are harder to secure In a LinkedIn study by NetBrain this year, because of: respondents indicated their biggest network • Lack of control and security problem is regulatory compliance. visibility But, all facets of network security received • More devices and traffic significant votes, suggesting security is a problem on the network across the board. • More tools to manage the network • The same number of Current Strategies to Confront These Challenges Come Up Short operations personnel There has been a lot of focus on device health monitoring, maintenance, and operations. This is because IT deploys very expensive machines to implement security designs, and they must protect the health of their investments. But, if the configuration and performance of those devices drift from their designed security intents, the effectiveness is lost even if device health appears optimal. This configuration drift, or sub- optimal settings, leads to the network being out of compliance and users experiencing degraded application performance. Often these huge vulnerabilities go undetected until the threat has already penetrated the network. We must not think of device health as the same as network health. Security Across the Hybrid Network | 2

"In order to close the gap between device health and network security, it is crucial for NetOps and SecOps organizations to shift their focus towards proactive measures, as opposed to relying predominantly on reactive approaches, which have traditionally been the preferred method. When end users detect issues that are not captured by device monitoring tools, they report them as incidents to the support team via ITSM tickets. This requires engineers to promptly respond, investigate, and resolve these unique problems. However, in the realm of security, by the time end users start encountering issues, it is already too late. The network has been compromised, and the business is likely experiencing financial losses. And worse, most issues that are assumed or treated as one-offs, typically have occurred before, sometimes many times, but the troubleshooting knowledge wasn’t captured for reuse. This results in repetitive work by valuable engineering resources costing time and leading to delayed incident responses, which in turn can lead to ticket backlogs. Add in the additional time delay when escalating more complex issues and the threat spreads further, you're MTTR averages start to suffer, and your organization becomes more at risk. It becomes a vicious cycle that's hard to escape. All of these represent reactionary procedures and protocols do not scale with networks and businesses as they expand. Traditionally, these teams could keep adding staff and resources, but now we’re at a point where experts are no longer an infinite resource. We have to evolve the current security operations strategy to help IT keep up with the business. Security Across the Hybrid Network | 3
Confronting the Challenges of Network Security But what does that evolution entail? What can we do to confront these challenges? 1. Expand visibility You can't manage what you can't see, but for large hybrid-cloud networks, it’s a problem of scale. We know adding every individual network component to our monitoring systems is cumbersome, time- and code-intensive. Automation offers a better way to discover your network and security policies and configurations. 2. Capture subject matter experts’ knowledge Nothing could ever match the creativity of human problem solving, not even AI. But why wait months or years nurturing AI to learn your network when unmatched expertise already resides in house? But, where humans come up short is efficiency, speed, and knowledge sharing across all levels of IT. The few experts an organization has are not available 24x7 and are stretched thin with other projects. A better way would be to capture troubleshooting experience so everyone can benefit from the steps and actions that expert took to resolve that issue, or a similar one. 3. Sharing knowledge across the organization When knowledge is harnessed, it can be leveraged by anyone to democratize operations at scale, reducing repetitive work and expediting troubleshooting. The ability to capture incidents and share and collaborate in real time reduces the need for escalations and hand- offs. Security Across the Hybrid Network | 4
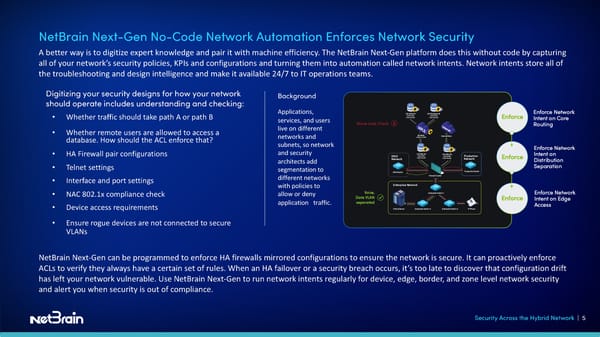
NetBrain Next-Gen No-Code Network Automation Enforces Network Security A better way is to digitize expert knowledge and pair it with machine efficiency. The NetBrain Next-Gen platform does this without code by capturing all of your network’s security policies, KPIs and configurations and turning them into automation called network intents. Network intents store all of the troubleshooting and design intelligence and make it available 24/7 to IT operations teams. Digitizing your security designs for how your network Background should operate includes understanding and checking: • Whether traffic should take path A or path B Applications, services, and users • Whether remote users are allowed to access a live on different database. How should the ACL enforce that? networks and subnets, so network • HA Firewall pair configurations and security • Telnet settings architects add segmentation to • Interface and port settings different networks with policies to • NAC 802.1x compliance check allow or deny • Device access requirements application traffic. • Ensure rogue devices are not connected to secure VLANs NetBrain Next-Gen can be programmed to enforce HA firewalls mirrored configurations to ensure the network is secure. It can proactively enforce ACLs to verify they always have a certain set of rules. When an HA failover or a security breach occurs, it’s too late to discover that configuration drift has left your network vulnerable. Use NetBrain Next-Gen to run network intents regularly for device, edge, border, and zone level network security and alert you when security is out of compliance. Security Across the Hybrid Network | 5
Complete Visibility NetBrain Next-Gen automates the discovery of the entire hybrid network and builds a live digital twin of devices, topology, flow, and intents. Multi-vendor support and dynamic mapping technologies mean no corner of your hybrid-cloud network ever goes unobserved. SIEM integrations allow for quick identification of devices and network paths to quickly respond to any incidents. NetBrain Next-Gen provides easy digestion of maps and intents to empower all levels of network support to collaborate and resolve situations quickly without escalation. Identify root causes and resolve issues earlier in the escalation path. Accelerate Malware Mitigation with One-IP Table With NetBrain Next-Gen, you can search any compromised endpoint or network device easily by IP address, MAC address, or DNS name. When your security or monitoring solution detects a device infected with malware, finding that device on the network can be like finding a needle in a haystack. But when security attacks occur, time is of the essence. Every second lost gives the malicious code more time to infect more devices and spread throughout the organization. You need to stop it in its tracks so you can lock down the network before personal data gets exfiltrated. NetBrain Next-Gen pinpoints the infected endpoint and the network devices it’s connected to so you can take immediate action. Whether you have the IP address, MAC address or DNS name, you can find the switchport its connected to so you can shut it down. Eliminate manual jumping from switch to switch searching ARP and MAC tables. A built-in One-IP Table gives you the ability to find any device on your network in seconds. So, when infected devices are detected, you can contain the spread. Security Across the Hybrid Network | 6
Continuous Monitoring and Enforcement of Network Security and Compliance Controls NetBrain Next-Gen uses proprietary no-code technology to capture your network’s security intents and stores them for use as executable automation tasks without scripting. NetBrain is 100% no-code. These are previously captured steps and actions. Save those intents that can then be replayed and applied to a completely new situation or new part of the network. Then, use these intents to proactively monitor security configurations and get alerted to deviations. But, even more, you can use those same intents proactively. Our research indicates 50% of all incidents are repetitive in nature, meaning that the same or similar issues have been reported in the past. IT knows how to solve these issues when they arise, and now we have the solutions captured as executable intents. Sometimes it takes hours for someone to respond to a ticket. Why not have those resolutions steps execute even before an engineering response to ticket you can have problem solving automation triggered as soon as an incident is reported to your IT assistant. By the time the support engineer acknowledges the ticket, NetBrain Next-Gen is already providing the root cause and recommended resolution steps. You can see all that from the ticket itself with our APIs and deep integration with the leading ITSM providers. Finally, we want to get to a point where we're preventing problems. There’s no need to wait for security breaches. Now, you can continuously verify and validate every part of your network security infrastructure. Those same intents used to share knowledge and troubleshoot can be leveraged to enforce security compliance. Security Across the Hybrid Network | 7
Auditing and Reporting NetBrain Next-Gen can help you get and stay in compliance and create customizable reports on the fly with the configurations included. It discovers the network in real-time and can produce exportable documentation in Microsoft Word and Visio. Reduce Risk with Protective Change Management Network change and configuration drift undermine implemented security measures over time resulting in more frequent and time-consuming security audits. Visualize infrastructure changes across the hybrid network and identify all impacted devices, services, and application dependencies –in seconds. Even successful device changes can result in unintended consequences. Now, ensure design intentions for network device changes and the resulting connectivity changes are preserved. Push security control changes at scale with verification and logging. Leverage rollbacks to quickly restore any previous configuration. Identify and push firmware updates to vulnerable or end of life devices. By pairing human decision-making knowledge with machine speed automation, you can eliminate repetitive workflows and significantly reduced meantime to repair. You can take any action that would take a human minutes or hours and have the machine do it for you in seconds, proactively. Your entire support infrastructure can leverage intents as automation when troubleshooting. Security Across the Hybrid Network | 8
Perform Regular Security Assessments Automation can help you mitigate rising costs and liability by providing continuous network assessments to ensure your business is always compliant. NetBrain Next-Gen takes the work out of assessments, so your engineers have a complete and real-time view of the network and its connectivity, performance, and security conditions. Understand how each of your network components supports and continuously verifies your business service delivery goals so you can defend your organization’s network architecture, change management workflows, and overall performance to meet application needs. Protect your hybrid network investments to create a foundation for network operations. Get Started Half of all respondents according to InformaTech’s 2022 State of Network Management report indicated security is their top network management priority, making it the top priority by a wide margin. What's held NetOps and SecOps back is getting the right technology into the right hands and NetBrain’s no-code automation is that platform. NetBrain Next-Gen transforms your network operations plan from an inefficient and reactive one, to a proactive, streamlined approach that leverages the knowledge and expertise you already have. It supports what you already have, and what you’ll have in the future, including all multi-vendor on-premises and public cloud components. It captures the expertise of your subject matter experts without any code to allow their knowledge to be replicated across the network and shared with their peers. NetBrain automation scales NetOps more efficiently, at a level previously only associated with additional headcount, higher costs and increased business risk. See In Action Security Across the Hybrid Network | 9
About NetBrain Technologies Founded in 2004, NetBrain is the market leader for NetOps automation, providing network operators and engineers with dynamic visibility across their hybrid networks and low-code/ no-code automation for key tasks across IT workflows. Today, more than 2,500 of the world’s largest enterprises and managed service providers use NetBrain to automate network problem diagnosis, generate real-time documentation, accelerate troubleshooting, and enforce enterprise architectural rules. +1 (800) 605-7964 | info@netbraintech.com | www.netbraintech.com Copyright © 2023 NetBrain Technologies, Inc. All trademarks referenced herein belong to NetBrain Technologies, Inc NB-EB-SATHN-052523